By the Authentix Brand Protection team
Brand protection often isn’t the first thing on a company’s mind as they launch a new product. When a company sets out to design a product, they want it to be a hit. They strive to make it useful and helpful to people, and they want their customers to trust and love the new product. Many brand owners refer to their products as their “baby” due to the long and challenging process to get it just right, in addition to the thought and testing that goes into the product research and development process.
One of the most powerful practices a company should apply to their products is often overlooked and that is brand protection, which can protect a company from unforeseen liability costs and customer mistrust in emerging or gray markets. Estimates vary, but the total amount of counterfeit goods impacting the job market is astonishing — it’s responsible for the loss of 2.5 million jobs globally.
When Brand Reputation is on the Line
An expression often used in sales states, “You are only as good as your last deal.” Similarly, brand reputation plays a significant role in the sales of most products. More than ever, customers are informed and do their research, reviewing competitors and finding the best deal according to various factors such as quality, cost, and reputation. A positive brand reputation can take years to build and only moments to collapse. (For example, in 2019, Nike pulled its products from the Amazon marketplace in part to try to lessen the damaging effects that counterfeit goods were then having on its brand). A brand’s positive reputation can be ruined due to a counterfeit product damaging someone’s skin, hair, body, or health.
Any product that is a premium brand and popular (e.g., car parts, cosmetics, pharmaceuticals, clothing, or even bed sheets) will be counterfeited at some point and can severely damage the reputation of the brand name. It can take many years and a significant amount of money in marketing and legal fees to rebuild public trust. The risk of this predicament can be materially reduced or even avoided with an investment in a brand protection program right from the start.
Forgoing Brand Protection Is Not an Option
When companies decide to forgo a brand protection program for the release of a premium product, several adverse outcomes can occur. The product may end up in non-targeted marketplaces where consumers find counterfeited or unauthorized and often heavily discounted versions. In many cases, this could also happen with brand owners’ third-party manufacturers producing unauthorized products for their own benefit.
In these cases, brand owners may also be held liable for those counterfeit products because there is little way to prove the provenance or authenticity of the fakes vs. the legitimately produced goods. For example, if a consumer in the marketplace gets hurt by an unauthorized or fake product, the brand owner is often exposed to liability. The legal fees can pile up quickly with no end in sight, all while product sales drop due to the lack of consumer trust.
In addition to counterfeited products, there is the gray market where consumers may find a company’s genuine products sold by unauthorized distributors at deeply discounted pricing, such as being sold out of the “back of the truck” or through other nonstandard channels. These may include expired or out-of-season products where the selling price is much less than the Minimum Advertised Price (MAP).
Supply Chain Physical Visibility & Traceability Simplified
Navigating a solid brand protection program does not have to be overly complex or challenging to implement. For example, putting a digital identifier or UIM on a product is much like putting a license plate on a car. That plate’s unique letter and number combinations should only be found on the exact vehicle with matching registration.
The same goes for placing a security taggant and/or a secure digital code on a product — it is only made for that specific product. The quantity and size of the product’s merchandising and packaging will determine the best security feature(s) needed to later identify the authenticity and unique attributes belonging to the product.
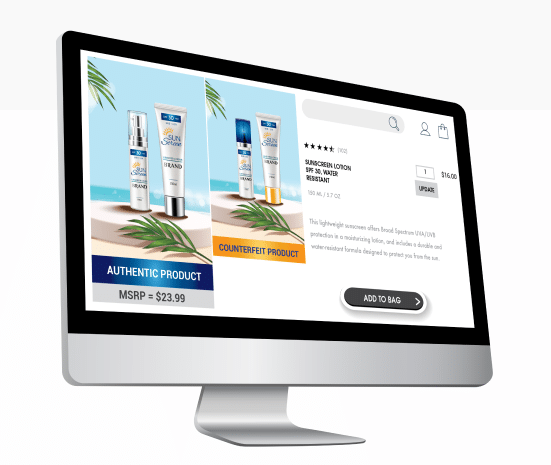
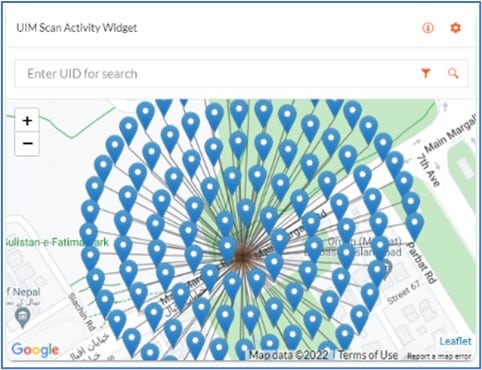
A covert or visible encrypted QR code with a unique, serialized item level ID can provide track-and-trace insight for a brand owner. This can provide much-needed supply chain visibility and uncover gray market diversion. If there is a question of the authenticity of a product, a consumer or inspector can check for various covert and/or overt security features (depending on the brand protection program the brand has in place).
For example, when a company’s product is entering the country of destination, the border patrol can easily detect the proper security taggants and confirm the validity of the product, allowing it to reach the distribution and retail channel much faster without delays in customs.
Online Brand Protection for Added Peace of Mind
Online brand protection is another factor to consider. If a product is sold in an online marketplace, there are tools today that can make the authentication process even easier. Many providers now have image searching and can digitally compare images for authorized licensed goods offered on non-authorized sites. Also, as part of online brand enforcement efforts, inspectors can view the product image for special overt security features to help identify these suspect products.
Today’s modern online brand protection advancements allow for identifying fake products and providing ancillary services such as cease-and-desist letters and a formal process to request site takedowns from legitimate or dark web marketplaces. Online brand protection services can perform sample buys and help find, chase, catch, and investigate infringing operators in multiple marketplaces, shutting them down and further protecting your trademark.
Consumer Engagement & Authentication Significant to Growth
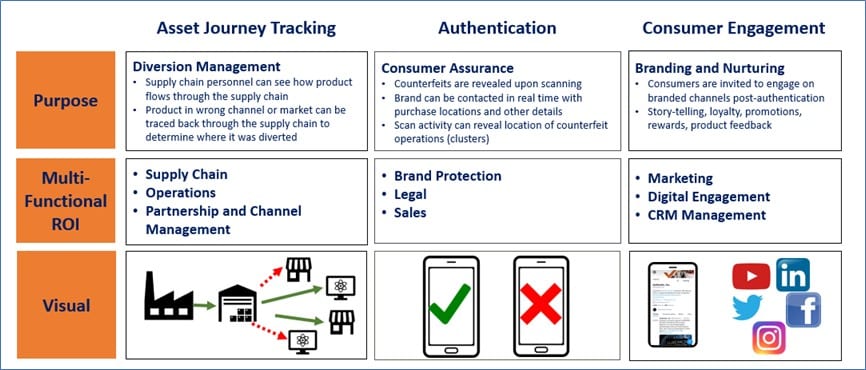
For traditional core brand protection programs, the growing trend of merging consumer engagement with digital product authentication in a single platform can be insightful for a growth-minded strategy. There are many technology options for both brand owners and authentication providers in developing these hybrid and dual-purpose programs. Such services allow consumer interaction for marketing purposes while forming large data sets to detect trends as the product’s journey is tracked.
As consumers become more vigilant and seek genuine products when shopping for premium brands, including a consumer engagement feature also provides an effective means of protecting products. Moreover, it enables direct engagement with loyal consumers to help increase both customer interaction and continued brand loyalty.
The Value of Complete Brand Protection
The return on investment of implementing a brand protection program from the beginning of a product’s introduction to the market is a valuable and worthwhile investment for several reasons. It can help detect fake or unauthorized products quickly, mitigate potential liability costs that may result, and help support a brand owner’s preferred market pricing by avoiding unauthorized gray market activity. Being able to police all third-party manufacturers can also be a crucial result of a well-implemented brand protection program.
About Authentix
As the authority in authentication solutions, Authentix brings enhanced visibility and traceability to today’s complex global supply chains. For over 25 years, Authentix has provided clients with physical and software-enabled solutions to detect, mitigate, and prevent counterfeiting and other illicit trading activity for currency, excise taxable goods, and branded consumer products. Through a proven partnership model and sector expertise, clients experience custom solution design, rapid implementation, consumer engagement, and complete program management to ensure product safety, revenue protection, and consumer trust for the best-known global brands on the market. Headquartered in Addison, Texas USA, Authentix, Inc. has offices in the North America, Europe, Middle East, Asia, and Africa serving clients worldwide. For more information, visit https://www.authentix.com.
Footnotes
1 BASCAP, Estimating the global economic and social impacts of counterfeiting and piracy, Frontier Economics, 2011
2 Elizabeth Segran, Nike tried playing nice with Amazon. Here’s why it didn’t work, Fast Company, 2019
 First, it is important to have registered IP rights and the ability to authenticate products efficiently. Second, the ability to collect and analyze high-quality data and manage a range of enforcement activity efficiently across hundreds of marketplaces globally is the most important factor in protecting IP. Authentix’s online brand protection solution and service platform gives our clients the ability to find and connect activities on a range of issues across ecommerce channels and further enables our global services team to manage these brand protection activities at scale. We also have active channels of communication with marketplaces to continuously address online threats collaboratively, and actively call out their lack of cooperation publicly.
First, it is important to have registered IP rights and the ability to authenticate products efficiently. Second, the ability to collect and analyze high-quality data and manage a range of enforcement activity efficiently across hundreds of marketplaces globally is the most important factor in protecting IP. Authentix’s online brand protection solution and service platform gives our clients the ability to find and connect activities on a range of issues across ecommerce channels and further enables our global services team to manage these brand protection activities at scale. We also have active channels of communication with marketplaces to continuously address online threats collaboratively, and actively call out their lack of cooperation publicly.